Remko Weijnen's Blog (Remko's Blog)
About Virtualization, VDI, SBC, Application Compatibility and anything else I feel like
This morning Arjan Beijer sent me an interesting link to a youtube video about obtaining the Citrix IMA Datastore password using Windbg.
The video shows a method, discovered by Denis Gundarev to obtain the IMA Datastore password. Basically he uses DSMaint.exe and set’s a breakpoint on the call to CryptUnprotectData and then reads the password from memory.
I tried to call the CryptUnprotectData API with the data read from the registry directly but this failed with error NTE_BAD_KEY_STATE, this is defined in winerror.h and it means “Key not valid for use in specified state”.
Entropy
I assumed Citrix was using an Entropy (salt) to make the decoding a little more difficult so I checked the disassembly from DSMaint with Ida Pro and it imports a function called GlobalData_GetDecryptedStrW from ImaSystem.dll:
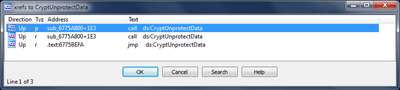
I openend ImaSystem.dll in Ida Pro and found CryptUnprotectData in the Imports Tab:
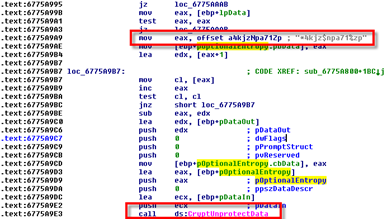
I checked the references (Ctrl-X) and went to the one on the top of the list:
I don’t think it’s difficult to spot the Entropy here?
Code
The code needed to decrypt the password is just a few lines:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | function Decrypt: String; var DataOut: DATA_BLOB; EntropyData: DATA_BLOB; begin EntropyData.cbData := Length(Entropy); EntropyData.pbData := @Entropy[1]; Win32Check(CryptUnProtectData(@DataIn, nil, @EntropyData, nil, nil, CRYPTPROTECT_UI_FORBIDDEN, @DataOut)); SetLength(Result, DataOut.cbData div SizeOf(Char)); CopyMemory(@Result[1], DataOut.pbData, DataOut.cbData); LocalFree(DWORD_PTR(DataOut.pbData)); end; |
Tool
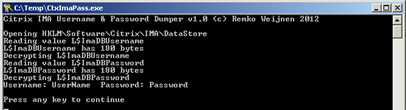
At the bottom of this post is a downloadable tool that reads the username and password data from the registry, decrypts and displays it:
Security Breach?
But where does this leave us? Is it a security breach?
I don’t think so, since the call to CryptUnprotectData fails if we do not have Admin privileges. Further more we can read the values remotely (if we have admin privileges) but we can only decrypt it locally.
Citrix IMA DataStore Username & Password Decoder (3234 downloads )Profile
Top Posts
- Query Active Directory from Excel
- RNS 510 Startup Logo–My thoughts
- Adding a hidden Exchange mailbox to Outlook
- How rdp passwords are encrypted
- Get Actual CPU Clock Speed with PowerShell
- ClickOnce Applications in Enterprise Environments
- VW RNS 510 Navigation Startup Pictures
- Unattended Installation of IBM System i Access for Windows
- Reading physical memory size from the registry
- Show Client IP Address when using NetScaler as a Reverse Proxy
Recent Comments
Featured Downloads
- AClientFix (13595 downloads )
- AddPrinter2.zip (12854 downloads )
- AdProps (12379 downloads )
- AdSample1 (11432 downloads )
- AMD Radeon Crimson ReLive (25268 downloads )
- Atheros Driver (34019 downloads )
- AutoLogonXP 1.0 (11404 downloads )
- CDZA (9560 downloads )
- ChDrvLetter.zip (11217 downloads )
- ChDrvLetter.zip (14356 downloads )
Blogroll
- Andrew Morgan
- Arnout’s blog
- Assa’s Blog
- Barry Schiffer
- Delphi Praxis
- Ingmar Verheij
- Jedi Api Blog
- Jedi API Library
- Jeroen Tielen
- Kees Baggerman
Categories
- .NET (4)
- Active Directory (28)
- Altiris (36)
- App-V (1)
- Apple (5)
- Application Compatibility (11)
- Automotive (5)
- AWS (1)
- BootCamp (1)
- C# (6)
- C++ (2)
- Citrix (87)
- Delphi (61)
- Embedded (4)
- Exchange (16)
- General (71)
- iPhone (5)
- Java (8)
- Linux (1)
- Lync (2)
- NetScaler (1)
- Oracle (4)
- Other (1)
- Packaging (19)
- PowerShell (56)
- Programming (79)
- Quest (1)
- RES (7)
- script (22)
- ShareFile (1)
- SQL Server (10)
- Strange Error (3)
- Terminal Server (68)
- ThinApp (3)
- ThinKiosk (1)
- Ubuntu (1)
- Unattended Installation (19)
- Uncategorized (51)
- UWP (2)
- Vista (37)
- Visual Studio (1)
- VMWare (26)
- Windows 10 (2)
- Windows 2003 (30)
- Windows 2008 (37)
- Windows 2008 R2 (16)
- Windows 2012 (2)
- Windows 7 (30)
- Windows 8 (4)
- Windows Internals (12)
- Windows XP (16)
Archives
- February 2023 (1)
- October 2022 (3)
- July 2022 (1)
- June 2022 (2)
- October 2019 (1)
- March 2018 (1)
- January 2018 (4)
- December 2017 (3)
- April 2017 (1)
- March 2017 (5)
- February 2017 (4)
- May 2016 (3)
- March 2016 (1)
- October 2015 (2)
- September 2015 (1)
- January 2015 (1)
- August 2014 (1)
- July 2014 (8)
- May 2014 (1)
- November 2013 (1)
- October 2013 (2)
- September 2013 (3)
- August 2013 (4)
- June 2013 (2)
- May 2013 (3)
- April 2013 (5)
- March 2013 (5)
- February 2013 (1)
- January 2013 (5)
- December 2012 (9)
- November 2012 (3)
- October 2012 (3)
- August 2012 (4)
- July 2012 (2)
- June 2012 (1)
- May 2012 (6)
- March 2012 (13)
- February 2012 (12)
- January 2012 (9)
- December 2011 (9)
- November 2011 (4)
- October 2011 (5)
- September 2011 (10)
- August 2011 (10)
- July 2011 (2)
- June 2011 (8)
- May 2011 (12)
- April 2011 (4)
- March 2011 (14)
- February 2011 (8)
- January 2011 (32)
- December 2010 (23)
- November 2010 (19)
- October 2010 (10)
- September 2010 (6)
- August 2010 (1)
- July 2010 (1)
- June 2010 (6)
- March 2010 (7)
- February 2010 (3)
- December 2009 (3)
- November 2009 (11)
- September 2009 (2)
- July 2009 (1)
- June 2009 (5)
- May 2009 (1)
- April 2009 (2)
- March 2009 (3)
- February 2009 (6)
- January 2009 (3)
- December 2008 (8)
- November 2008 (5)
- October 2008 (3)
- September 2008 (3)
- August 2008 (3)
- June 2008 (6)
- May 2008 (2)
- April 2008 (3)
- March 2008 (5)
- January 2008 (3)
- December 2007 (3)
- November 2007 (13)
- October 2007 (10)

4 Responses for "Decoding Citrix IMA Datastore Password"
great article remko! i tried the tool but just getting: seems that L$ImaDBUsername could not converted correctly?!
Citrix IMA Username & Password Dumper v1.0 (c) Remko Weijnen 2012
Opening HKLM\Software\Citrix\IMA\DataStore
Reading value L$ImaDBUsername
L$ImaDBUsername has 164 bytes
Decrypting L$ImaDBUsername
EOSError: System Error. Code: 13.
The data is invalid
Press any key to continue
Thanks Andreas, it was a little bug in my tool. I fixed it and uploaded a new version.
Great! i’m lost the sa password of a sql 2008 r2 express datastore…. thank’s!!
i get the following:
Citrix IMA Username & Password Dumper v1.0 (c) Remko Weijnen 2012
Opening HKLM\Software\Citrix\IMA\DataStore
Reading value L$ImaDBUsername
L$ImaDBUsername has 188 bytes
Decrypting L$ImaDBUsername
EOSError: System Error. Code: -2146893813.
Key not valid for use in specified state
Press any key to continue
Please advise
Leave a reply