Remko Weijnen's Blog (Remko's Blog)
About Virtualization, VDI, SBC, Application Compatibility and anything else I feel like
 One of my colleagues asked me to assist in troubleshooting an application called SmartWare FM running on Citrix XenApp.
One of my colleagues asked me to assist in troubleshooting an application called SmartWare FM running on Citrix XenApp.
This application reads data from an external device called SECUTEST.
The device is connected to a COM port which is redirected to the XenApp session. In contrast to Microsoft Remote Desktop Services COM ports are not automatically redirected in XenApp but need to be mapped via eg a logonscript (NET USE COM1: \\Client\COM1:) or using UEM.
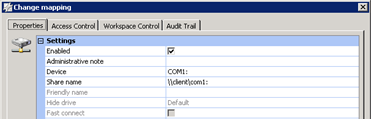
In my case the COM port was mapped with RES Workspace Manager:
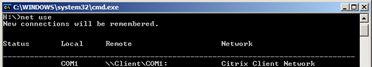
I verified using net use that the com port is actually mapped:
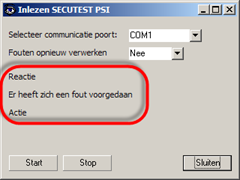
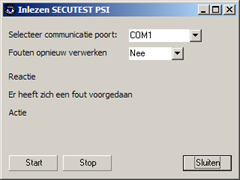
The import in the application fails however with a generic error (Er heeft zich een fout voorgedaan):
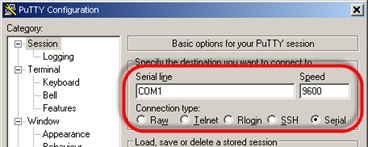
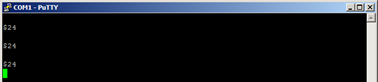
I disconnected the XenApp session and ran Putty locally connected to COM1 9600-N-8-1.
Pressing enter echoes $24 (apparently some kind of protocol) so the communication between PC and device seems to work:
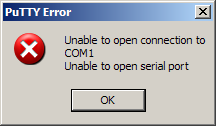
I then tried to connect with Putty (a lightweight terminal client)from within the XenApp session but got an immediate connection failure:
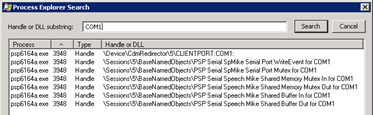
This message normally appears when a COM port is already in use so I opened Process Explorer and used Find | Find Handle or DLL and searched for COM1:
CdmRedirector is the Client Device Mapping redirector from Citrix so it appears that our COM port is already connected to the psp6164a.exe process.
psp6164a.exe belongs to Philips G2 Speech and seems to be responsible for communication to serial G2 Speech devices. The executable is launched from the HKLM run key:
I knew that in this environment only USB connected G2 Speech devices are used but I wanted to check if there was some kind of commandline argument I could set to skip COM1.
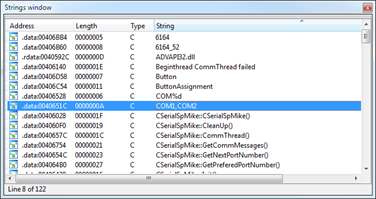
I opened psp6164a.exe in Ida Pro and searched for COM1:
Using Ctrl-X (references) I ended up in this code:
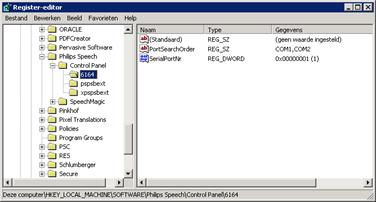
Using the registry (HKLM\SOFTWARE\Philips Speech\Control Panel\6164) we can configure the active port and Port Search Order:
After reconfiguring I retested with Putty and the communication seemed to work from within the XenApp session:
However the application failed with the same error:
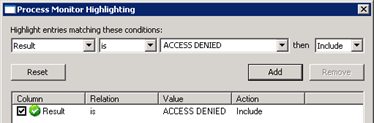
Knowing that the connection and protocol were working I monitored with Process Monitor. I usually focus on ACCESS DENIED errors by using the Filter | Highlight option to easily identify them:
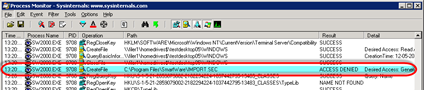
There was just one:
Looks like the application tries to write a file to the Program Files folder (why do developers insist on doing this?).
We can of course give the users write permissions on this folder or perhaps even this file but what happens when multiple users try to do this at the same time?
A better solution is to use an Application Compatibility shim to redirect this file to a user specific and user writable location. I choose to redirect it to H:\Windows\Temp (H:\ is the users homefolder).
But we need to verify if there are any other files we need to redirect either by trial and error or search for related files.
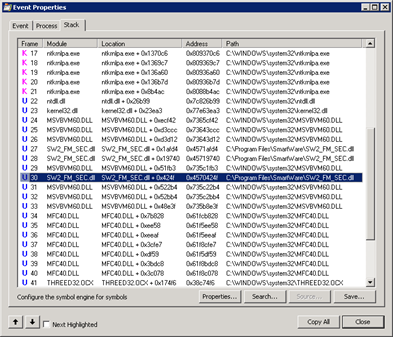
I double-clicked the line that resulted in ACCESS DENIED in Process Monitor and switched to the Stack tab. There was only one file from the Applications folder in there called SW2_FM_SEC.dll:
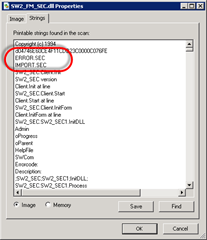
I opened Process Explorer, clicked the Applications executable and set the Lower Pane View to DLLs. Then I selected SW2_FM_SEC.dll from the list and listed it’s properties, on the Strings tab we can see that besides IMPORT.SEC there is probably a file called ERROR.SEC:
So let’s create the redirect shim (if you are new to Application Compatibility read this article first).
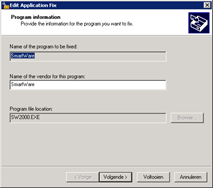
Create a new database and the executable (SW2000.exe in my case):
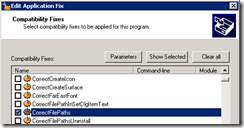
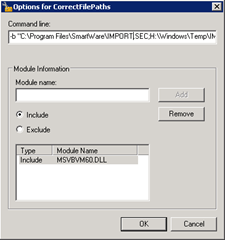
Select the CorrectFilePath Shim and click Parameters:
Note that MSVBVM60.DLL is on stack (in the Process Monitor screenshot above) so we need to add MSVBVM60.DLL to the include modules (see here for an explanation).
The Command line is:
1 | -b "C:\Program Files\SmartWare\IMPORT.SEC;H:\Windows\Temp\IMPORT.SEC" "C:\Program Files\SmartWare\ERROR.SEC;H:\Windows\Temp\ERROR.SEC" |
Save and install the database and now everything works correctly:
Of course you need to distribute and install the Shim to your production environment, more about that here.
Profile
Top Posts
- Query Active Directory from Excel
- RNS 510 Startup Logo–My thoughts
- Adding a hidden Exchange mailbox to Outlook
- How rdp passwords are encrypted
- Get Actual CPU Clock Speed with PowerShell
- ClickOnce Applications in Enterprise Environments
- VW RNS 510 Navigation Startup Pictures
- Unattended Installation of IBM System i Access for Windows
- Reading physical memory size from the registry
- Show Client IP Address when using NetScaler as a Reverse Proxy
Recent Comments
Featured Downloads
- AClientFix (13595 downloads )
- AddPrinter2.zip (12854 downloads )
- AdProps (12379 downloads )
- AdSample1 (11432 downloads )
- AMD Radeon Crimson ReLive (24044 downloads )
- Atheros Driver (34019 downloads )
- AutoLogonXP 1.0 (11404 downloads )
- CDZA (9560 downloads )
- ChDrvLetter.zip (11217 downloads )
- ChDrvLetter.zip (14356 downloads )
Blogroll
- Andrew Morgan
- Arnout’s blog
- Assa’s Blog
- Barry Schiffer
- Delphi Praxis
- Ingmar Verheij
- Jedi Api Blog
- Jedi API Library
- Jeroen Tielen
- Kees Baggerman
Categories
- .NET (4)
- Active Directory (28)
- Altiris (36)
- App-V (1)
- Apple (5)
- Application Compatibility (11)
- Automotive (5)
- AWS (1)
- BootCamp (1)
- C# (6)
- C++ (2)
- Citrix (87)
- Delphi (61)
- Embedded (4)
- Exchange (16)
- General (71)
- iPhone (5)
- Java (8)
- Linux (1)
- Lync (2)
- NetScaler (1)
- Oracle (4)
- Other (1)
- Packaging (19)
- PowerShell (56)
- Programming (79)
- Quest (1)
- RES (7)
- script (22)
- ShareFile (1)
- SQL Server (10)
- Strange Error (3)
- Terminal Server (68)
- ThinApp (3)
- ThinKiosk (1)
- Ubuntu (1)
- Unattended Installation (19)
- Uncategorized (51)
- UWP (2)
- Vista (37)
- Visual Studio (1)
- VMWare (26)
- Windows 10 (2)
- Windows 2003 (30)
- Windows 2008 (37)
- Windows 2008 R2 (16)
- Windows 2012 (2)
- Windows 7 (30)
- Windows 8 (4)
- Windows Internals (12)
- Windows XP (16)
Archives
- February 2023 (1)
- October 2022 (3)
- July 2022 (1)
- June 2022 (2)
- October 2019 (1)
- March 2018 (1)
- January 2018 (4)
- December 2017 (3)
- April 2017 (1)
- March 2017 (5)
- February 2017 (4)
- May 2016 (3)
- March 2016 (1)
- October 2015 (2)
- September 2015 (1)
- January 2015 (1)
- August 2014 (1)
- July 2014 (8)
- May 2014 (1)
- November 2013 (1)
- October 2013 (2)
- September 2013 (3)
- August 2013 (4)
- June 2013 (2)
- May 2013 (3)
- April 2013 (5)
- March 2013 (5)
- February 2013 (1)
- January 2013 (5)
- December 2012 (9)
- November 2012 (3)
- October 2012 (3)
- August 2012 (4)
- July 2012 (2)
- June 2012 (1)
- May 2012 (6)
- March 2012 (13)
- February 2012 (12)
- January 2012 (9)
- December 2011 (9)
- November 2011 (4)
- October 2011 (5)
- September 2011 (10)
- August 2011 (10)
- July 2011 (2)
- June 2011 (8)
- May 2011 (12)
- April 2011 (4)
- March 2011 (14)
- February 2011 (8)
- January 2011 (32)
- December 2010 (23)
- November 2010 (19)
- October 2010 (10)
- September 2010 (6)
- August 2010 (1)
- July 2010 (1)
- June 2010 (6)
- March 2010 (7)
- February 2010 (3)
- December 2009 (3)
- November 2009 (11)
- September 2009 (2)
- July 2009 (1)
- June 2009 (5)
- May 2009 (1)
- April 2009 (2)
- March 2009 (3)
- February 2009 (6)
- January 2009 (3)
- December 2008 (8)
- November 2008 (5)
- October 2008 (3)
- September 2008 (3)
- August 2008 (3)
- June 2008 (6)
- May 2008 (2)
- April 2008 (3)
- March 2008 (5)
- January 2008 (3)
- December 2007 (3)
- November 2007 (13)
- October 2007 (10)



6 Responses for "The case of the COM Port Redirection"
Kinda awesome. However, does also leave me with bewildered. I mean, it’s nice that you _can_ solve this.
But it is really crappy that you have to, in the first place. Why don’t we switch to quality software that was actually written this century?
Either that, or, why don’t we keep these applications on their intended platform? I mean, you are basically sewing together a backwards compatible virtual machine from various components (XenApp/RDP, RES manager, Application virtualization, (UAC?) virtualization, compatibility shims, what not).
FrankenPC!
Do we ever wonder why our software delivery fails to get robust?
How many paid products were used in trying to make other paid products work as advertised?
(Also, I wager that there would have been a decent chance of fixing the file access problems by having SW2000.EXE start from a safe working directory (there is a reasonable chance that it just accesses these files by relative paths).)
Still awesome war story. Thanks for sharing, seriously. It does inspire me at least as much as it saddens me 🙂
@sehe: thanks for your comment, it’s good to have a discussion about it so thanks for that!
My reply below is not specifically about this application but more in general.
I often call badly behaving applications “Crapplications” just to emphasize how badly written they are. I would like nothing more than to keep Crapplications out and replace them with better written software (from a technical view).
As an external consultant I usually don’t have such powers, I am just brought in to make it work. In fact often the IT department doesn’t have such power since the business simply dictates IT what to do. And from the business perspective the Crapplication often perfectly supports their business process.
Medical applications often required FDA approval (may take years) which is a big hurdle to take when deciding to rewrite the software.
As for this application specific:
I agree that it’s likely we can install this application into a different path, question is if that will really fix our problem. On a multi user system it still means that multiple users might write into this file at the same time!
In a migration scenario it’s often not even possible to change paths since the configuration files (think ini’s on a share) are usually shared.
Still I agree with you: I would really like to see the day where all of these skills are not required anymore 😀
[…] Yesterday I wrote about troubleshooting an application that used Com Port redirection in Citrix. […]
[I agree that it
[…] The case of the COM Port Redirection […]
[…] Für unser zweites Treffen am 19.03. in Köln haben wir Remko Weijnen als Referent gewinnen können. Wir kennen und schätzen ihn schon lange. Ich selbst (Helge) wurde zunächst auf sein exzellentes Blog aufmerksam und traf ihn bald darauf auch auf den E2EVC-Konferenzen (die, nebenbei bemerkt, immer eine Reise Wert sind). Dort erstaunte er die Zuhörerschaft immer wieder mit seinem Wissen rund um Anwendungskompatibilität und -sicherheit. Er zeigte dabei unter anderem, wie sich auch sehr störrische Anwendungen durch detaillierte Analyse und anschließendes Patchen unter XenApp zum Laufen gebracht werden können. In vielen Fällen kann auf eine Modifikation der Binärdateien verzichtet werden und es können stattdessen Kompatibilitäts-Shims zum Einsatz kommen, wie hier von Remko beschrieben. […]
Leave a reply