Remko Weijnen's Blog (Remko's Blog)
About Virtualization, VDI, SBC, Application Compatibility and anything else I feel like
Recently I published a Proof of Concept that showed it was possible to launch unauthorized processes with both AppSense Application Manager and RES Workspace Manager.
Although I didn’t test Microsoft Applocker I have no doubt at all that we couldn’t bypass it.
 I have named my Proof of Concept the XLSploit because I am using Excel as a trampoline. I choose Excel because this is generally a trusted process and VBA offers access to the Windows API that is needed.
I have named my Proof of Concept the XLSploit because I am using Excel as a trampoline. I choose Excel because this is generally a trusted process and VBA offers access to the Windows API that is needed.
After publishing the XLSploit I have talked to both RES and AppSense and not that they both have a response to my Proof of Concept, I consider it safe to tell a little more about how it works.
If you are merely interested in stopping the XLSploit, please scroll down to the end of the article.
How does it work?
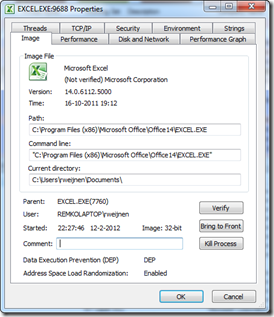
From a trusted process we launch another copy of any trusted process (the Host Process) using the CreateProcess API. In my case I am launching a second instance of Excel from Excel.
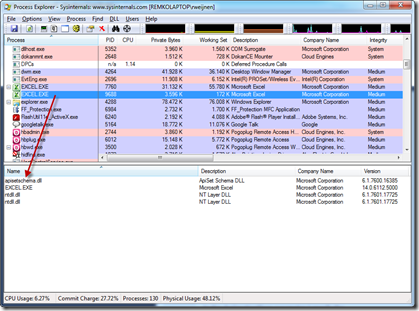
In the dwCreationFlags parameter I specify the CREATE_SUSPENDED Process Flag. This will start the process but it will halt after loading ntdll.dll and before executing the Loader Routine. We can see this in Process Explorer, the process is highlighted in gray which indicates it’s in suspended state:
Now we load the process that we actually want to launch (the Target Process), but instead of calling the CreateProcess API we load it in memory as a binary file.
You may have guessed the idea by now: we are going to “replace” the suspended process in memory with the contents we read from disk.
This means we first need to get the address of the PEB (Process Environment Block) using the GetThreadContext API. The PEB Address is in the EBX field of the retrieved CONTEXT structure.
Using the ReadProcessMemory API we read the Image Base Address from the PEB and unmap it from the Host Process.
Using the IMAGE_DOS_HEADER, IMAGE_NT_HEADERS we can analyze the target process and copy it’s contents to the memory space of the Host Process.
Depending on the OS we need to do some fixups such as base relocations, account for Side By Side manifests and MUI resources.
After that we set the Thread Context using the SetThreadContext API to the entry point of the Target Process and resume the process using the ResumeThread API.
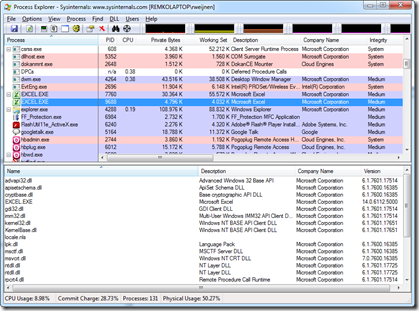
After resuming we seem to have a second instance of Excel.exe:
Even the Window Title shows Excel:
Even Process Explorer shows that we are running Excel:
Is it an Excel Exploit?
No! We could use any trusted process for this exploit that offers us access to the Windows API. The convenience of VBA in Office is that it allows us full access to the Windows API.
Is it a Windows Exploit?
No, I don’t think so. The Windows security model protects you from the outside (think other computers) and from other users. It does not protect you from yourself; you have permissions to open, debug, kill, do anything with your own processes.
Is it malware?
The XLSploit is not malware, it doesn’t damage your system in any way. However the code does things that are typically associated with malware. Therefore your Virus Scanner should at least find it suspicious. The strange thing is that if I place similar code in an executable or DLL, all Virus Scanners alert. But when used from VBA most Virus Scanners seem to allow it.
What it does not do
Using this method we can successfully launch unauthorized processes, however we do not gain additional privileges (aka privilege escalation). If you are a standard user, you still will not have permissions to delete system folders and files. It could of course be a first step towards that but we would need other exploits for it.
How to stop this Exploit?
First of all: you should set Office Macro Security to High and prevent users from changing it. I know this probably breaks all applications you use, so you should really put pressure on your vendors and have them sign their macro’s. Or as an alternative, self sign them.
Secondly: Implement A Virus Scanner that uses the Office AntiVirus API to scan documents and macro’s. Most Home versions of AV products seem to have this while Enterprise products often do not. Perhaps because of performance reasons.
For RES Workspace Manager see: Q203322 HOWTO: How to prevent malicious Microsoft Office macros and here.
For AppSense Application Manager see: AppSense Blog
Profile
Top Posts
- Query Active Directory from Excel
- RNS 510 Startup Logo–My thoughts
- Adding a hidden Exchange mailbox to Outlook
- How rdp passwords are encrypted
- Get Actual CPU Clock Speed with PowerShell
- ClickOnce Applications in Enterprise Environments
- VW RNS 510 Navigation Startup Pictures
- Unattended Installation of IBM System i Access for Windows
- Reading physical memory size from the registry
- Show Client IP Address when using NetScaler as a Reverse Proxy
Recent Comments
Featured Downloads
- AClientFix (13595 downloads )
- AddPrinter2.zip (12854 downloads )
- AdProps (12379 downloads )
- AdSample1 (11432 downloads )
- AMD Radeon Crimson ReLive (24847 downloads )
- Atheros Driver (34019 downloads )
- AutoLogonXP 1.0 (11404 downloads )
- CDZA (9560 downloads )
- ChDrvLetter.zip (11217 downloads )
- ChDrvLetter.zip (14356 downloads )
Blogroll
- Andrew Morgan
- Arnout’s blog
- Assa’s Blog
- Barry Schiffer
- Delphi Praxis
- Ingmar Verheij
- Jedi Api Blog
- Jedi API Library
- Jeroen Tielen
- Kees Baggerman
Categories
- .NET (4)
- Active Directory (28)
- Altiris (36)
- App-V (1)
- Apple (5)
- Application Compatibility (11)
- Automotive (5)
- AWS (1)
- BootCamp (1)
- C# (6)
- C++ (2)
- Citrix (87)
- Delphi (61)
- Embedded (4)
- Exchange (16)
- General (71)
- iPhone (5)
- Java (8)
- Linux (1)
- Lync (2)
- NetScaler (1)
- Oracle (4)
- Other (1)
- Packaging (19)
- PowerShell (56)
- Programming (79)
- Quest (1)
- RES (7)
- script (22)
- ShareFile (1)
- SQL Server (10)
- Strange Error (3)
- Terminal Server (68)
- ThinApp (3)
- ThinKiosk (1)
- Ubuntu (1)
- Unattended Installation (19)
- Uncategorized (51)
- UWP (2)
- Vista (37)
- Visual Studio (1)
- VMWare (26)
- Windows 10 (2)
- Windows 2003 (30)
- Windows 2008 (37)
- Windows 2008 R2 (16)
- Windows 2012 (2)
- Windows 7 (30)
- Windows 8 (4)
- Windows Internals (12)
- Windows XP (16)
Archives
- February 2023 (1)
- October 2022 (3)
- July 2022 (1)
- June 2022 (2)
- October 2019 (1)
- March 2018 (1)
- January 2018 (4)
- December 2017 (3)
- April 2017 (1)
- March 2017 (5)
- February 2017 (4)
- May 2016 (3)
- March 2016 (1)
- October 2015 (2)
- September 2015 (1)
- January 2015 (1)
- August 2014 (1)
- July 2014 (8)
- May 2014 (1)
- November 2013 (1)
- October 2013 (2)
- September 2013 (3)
- August 2013 (4)
- June 2013 (2)
- May 2013 (3)
- April 2013 (5)
- March 2013 (5)
- February 2013 (1)
- January 2013 (5)
- December 2012 (9)
- November 2012 (3)
- October 2012 (3)
- August 2012 (4)
- July 2012 (2)
- June 2012 (1)
- May 2012 (6)
- March 2012 (13)
- February 2012 (12)
- January 2012 (9)
- December 2011 (9)
- November 2011 (4)
- October 2011 (5)
- September 2011 (10)
- August 2011 (10)
- July 2011 (2)
- June 2011 (8)
- May 2011 (12)
- April 2011 (4)
- March 2011 (14)
- February 2011 (8)
- January 2011 (32)
- December 2010 (23)
- November 2010 (19)
- October 2010 (10)
- September 2010 (6)
- August 2010 (1)
- July 2010 (1)
- June 2010 (6)
- March 2010 (7)
- February 2010 (3)
- December 2009 (3)
- November 2009 (11)
- September 2009 (2)
- July 2009 (1)
- June 2009 (5)
- May 2009 (1)
- April 2009 (2)
- March 2009 (3)
- February 2009 (6)
- January 2009 (3)
- December 2008 (8)
- November 2008 (5)
- October 2008 (3)
- September 2008 (3)
- August 2008 (3)
- June 2008 (6)
- May 2008 (2)
- April 2008 (3)
- March 2008 (5)
- January 2008 (3)
- December 2007 (3)
- November 2007 (13)
- October 2007 (10)

3 Responses for "The XLSploit explained"
Very impressive Remko!
This shows us that we should consider security more often instead of “fixing” poorly written macro’s in Office apps.
PS: Good to see the vendors responded so quickly with a solution.
Thank you Remko for giving us such a clear and detailed explaination of the XLSploit.
Great blog to make us remember the reason for the macro security in Office.
Great to also be linked to the quick responses and solution directives from RES Software and Appsense.
[…] the app guard by running other processes in memory using a simple macro. You can read about it here. RES implemented a feature in Workspace Manager where you can narrow the security by allowing only […]
Leave a reply