Remko Weijnen's Blog (Remko's Blog)
About Virtualization, VDI, SBC, Application Compatibility and anything else I feel like
Recently I stumbled upon an executable that appeared to be a PowerShell script converted into an executable.
I was curious to the actual script so I decided to have a look and see how I could convert the executable back into PowerShell.
Having seen similar techniques to turn vb scripts and java jar’s into executables I first looked if this particular executable was simply carrying the payload in the resource section.
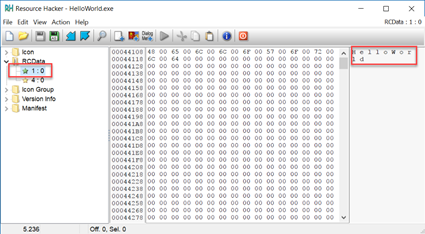
I opened the executable with Resource Hacker and saw 2 resources (note that I am using a simple HelloWorld executable here in the screenshots). The first resource, named 1, is clearly a Unicode string with the title:
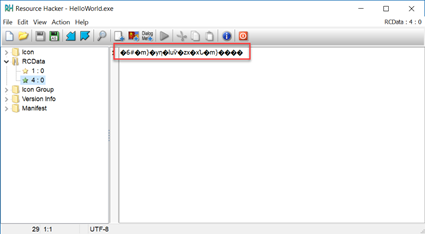
The second resource, named 4 is probably carrying the payload and is encrypted or obfuscated:
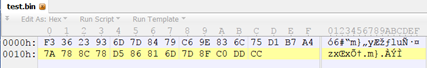
I saved the resource as a .bin file and inspected it with a hex viewer:
The code turned out to be AES encrypted and I wrote a tool to decrypt it. As the decrypted code had a comment line Code generated by: SAPIEN Technologies, Inc., PowerShell Studio 2016 v5.3.130 I could conclude that it was compiled using Sapien PowerShell Studio.
I asked a few PowerShell people I know to test my decryptor and they came back with positive results. In this testing I noticed that there were some different variants of the code that Sapien uses and so far I have identified 3 different ones which can be decrypted.
One tester noted of a different tool, ISESteroids, that can also convert PowerShell scripts into executables. ISESteroids uses a different technique but the decryptor tool also supports it.
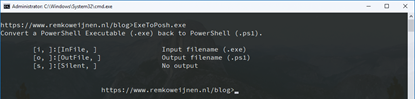
The decryptor has the following commandline arguments:
Note that the tool comes in both 32- and 64 bit versions so you need to use the one that matches your binaries bitness (else you will get a System.BadImageFormatException).
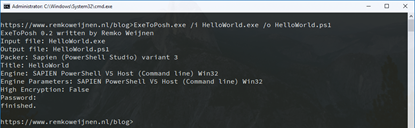
Here’s an example of using it:
Update 16-9-2020: Google is flagging my site as one that serves malicous files because ExeToPosh is triggering some antivirus products (false positives). As Google doesn’t respond to my clarifications I have published the source code on GitHub. This allows everyone to ensure there is no included malware, alternatively if you do trust me you can fetch the binary from the releases section on Github.
Profile
Top Posts
- Query Active Directory from Excel
- RNS 510 Startup Logo–My thoughts
- Adding a hidden Exchange mailbox to Outlook
- How rdp passwords are encrypted
- Get Actual CPU Clock Speed with PowerShell
- ClickOnce Applications in Enterprise Environments
- VW RNS 510 Navigation Startup Pictures
- Unattended Installation of IBM System i Access for Windows
- Reading physical memory size from the registry
- Show Client IP Address when using NetScaler as a Reverse Proxy
Recent Comments
Featured Downloads
- AClientFix (13595 downloads )
- AddPrinter2.zip (12854 downloads )
- AdProps (12379 downloads )
- AdSample1 (11432 downloads )
- AMD Radeon Crimson ReLive (30229 downloads )
- Atheros Driver (34019 downloads )
- AutoLogonXP 1.0 (11404 downloads )
- CDZA (9560 downloads )
- ChDrvLetter.zip (11217 downloads )
- ChDrvLetter.zip (14356 downloads )
Blogroll
- Andrew Morgan
- Arnout’s blog
- Assa’s Blog
- Barry Schiffer
- Delphi Praxis
- Ingmar Verheij
- Jedi Api Blog
- Jedi API Library
- Jeroen Tielen
- Kees Baggerman
Categories
- .NET (4)
- Active Directory (28)
- Altiris (36)
- App-V (1)
- Apple (5)
- Application Compatibility (11)
- Automotive (5)
- AWS (1)
- BootCamp (1)
- C# (6)
- C++ (2)
- Citrix (87)
- Delphi (61)
- Embedded (4)
- Exchange (16)
- General (71)
- iPhone (5)
- Java (8)
- Linux (1)
- Lync (2)
- NetScaler (1)
- Oracle (4)
- Other (1)
- Packaging (19)
- PowerShell (56)
- Programming (79)
- Quest (1)
- RES (7)
- script (22)
- ShareFile (1)
- SQL Server (10)
- Strange Error (3)
- Terminal Server (68)
- ThinApp (3)
- ThinKiosk (1)
- Ubuntu (1)
- Unattended Installation (19)
- Uncategorized (51)
- UWP (2)
- Vista (37)
- Visual Studio (1)
- VMWare (26)
- Windows 10 (2)
- Windows 2003 (30)
- Windows 2008 (37)
- Windows 2008 R2 (16)
- Windows 2012 (2)
- Windows 7 (30)
- Windows 8 (4)
- Windows Internals (12)
- Windows XP (16)
Archives
- February 2023 (1)
- October 2022 (3)
- July 2022 (1)
- June 2022 (2)
- October 2019 (1)
- March 2018 (1)
- January 2018 (4)
- December 2017 (3)
- April 2017 (1)
- March 2017 (5)
- February 2017 (4)
- May 2016 (3)
- March 2016 (1)
- October 2015 (2)
- September 2015 (1)
- January 2015 (1)
- August 2014 (1)
- July 2014 (8)
- May 2014 (1)
- November 2013 (1)
- October 2013 (2)
- September 2013 (3)
- August 2013 (4)
- June 2013 (2)
- May 2013 (3)
- April 2013 (5)
- March 2013 (5)
- February 2013 (1)
- January 2013 (5)
- December 2012 (9)
- November 2012 (3)
- October 2012 (3)
- August 2012 (4)
- July 2012 (2)
- June 2012 (1)
- May 2012 (6)
- March 2012 (13)
- February 2012 (12)
- January 2012 (9)
- December 2011 (9)
- November 2011 (4)
- October 2011 (5)
- September 2011 (10)
- August 2011 (10)
- July 2011 (2)
- June 2011 (8)
- May 2011 (12)
- April 2011 (4)
- March 2011 (14)
- February 2011 (8)
- January 2011 (32)
- December 2010 (23)
- November 2010 (19)
- October 2010 (10)
- September 2010 (6)
- August 2010 (1)
- July 2010 (1)
- June 2010 (6)
- March 2010 (7)
- February 2010 (3)
- December 2009 (3)
- November 2009 (11)
- September 2009 (2)
- July 2009 (1)
- June 2009 (5)
- May 2009 (1)
- April 2009 (2)
- March 2009 (3)
- February 2009 (6)
- January 2009 (3)
- December 2008 (8)
- November 2008 (5)
- October 2008 (3)
- September 2008 (3)
- August 2008 (3)
- June 2008 (6)
- May 2008 (2)
- April 2008 (3)
- March 2008 (5)
- January 2008 (3)
- December 2007 (3)
- November 2007 (13)
- October 2007 (10)

11 Responses for "Convert Executable to PowerShell"
Good job but the download link doesn’t work! Thanks for sharing 😉
The download works now! 🙂
Everything so nice , so much work done, and here you are not providing source code or anything else that the exe, you sure should work for Microsoft.
I’m not sure what bashing Microsoft adds here. With regards to the source code I have reasons for not publishing it. Goal was enable you to read exe powershell scripts before executing and that has been accomplished…
Not sure why you are responding so harsh, I have good reasons for not publishing the source code… The goal was to be able to view what’s inside PowerShell Executables and that has been accomplished.
Too bad it looks like it has a trojan in it. I was hoping for a real solution, not to get my enterprise owned.
Hi Reggie, I can tell you the alerts is a false positive and I’ve even reported that to several AV vendors but sadly due to the nature of the program (encryption and loading resources from exe) it flags some AV’s.
If you don’t trust me on this, try it in a VM or a sandbox solution such as Sandboxie.
Hi Remko,
When using your tool it say’s “password ????????????>??????????” and the output is still encrypted. Do you know why? Can you tell more about how you found the key and IV?
Cheers,
Squ1zZy
There’s a document online how to decrypt an executable using a newer version of PowerShell Studio:
https://www.thalpius.com
Hey mate, thanks for writing this.
i tried it today and am getting the following
C:\Temp>ExeToPosh.exe /i Monitor.exe /o test.ps1
ExeToPosh 0.2 written by Remko Weijnen
Input file: Monitor.exe
Output file: test.ps1
Packer: Sapien (PowerShell Studio) variant 3
Unhandled Exception: System.ArgumentNullException: Value cannot be null.
Parameter name: source
at System.Runtime.InteropServices.Marshal.CopyToManaged(IntPtr source, Object destination, Int32 startIndex, Int32 length)
at ExeToPosh.Program.LoadProperties(Assembly ass)
at ExeToPosh.Program.Main(String[] args)
followed by a crash window.
I am running the x64 version on x64 win 10 1803, under an elevated command prompt.
any suggestions ?
Can you share the exe?
Leave a reply