Remko Weijnen's Blog (Remko's Blog)
About Virtualization, VDI, SBC, Application Compatibility and anything else I feel like
Archive for December, 2017
Sign APPX packages with PowerShell
Author: Remko Weijnen20 Dec
I have been working with Microsoft’s Desktop App Converter a lot recently. Even though there’s an option to autosign the resulting package with the -Sign switch I prefer to sign APPX packages myself using signtool.
The reason is that I can send UWP packages to testers for sideloading without requiring them to import the auto generated certificate (which is different on each (re)build).
However I always forget the exact path to signtool.exe (this comes with the Windows SDK).
The Windows 10 SDK is installed by default in C:\Program Files (x86)\Windows Kits\10.
Signtool.exe will be in the folder<sdkpath>\bin\<version>\<platform>\signtool.exe.
As there are multiple version of Windows 10 there are multiple version of the SDK and you can install those concurrently.
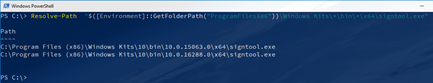
But then I found the PowerShell cmdlet Resolve-Path which “Resolves the wildcard characters in a path, and displays the path contents”.
This does exactly what I need:
Wow, Resolve-Path is a perfect example of the many hidden gems in PowerShell!
So I decided to wrap signtool.exe in a PowerShell cmdlet as PowerShell also makes it easy to locate the correct code signing certificate from the certificate store. (more…)
RAD Studio Tokyo 10.2(.2) Data Collection
Author: Remko Weijnen18 Dec
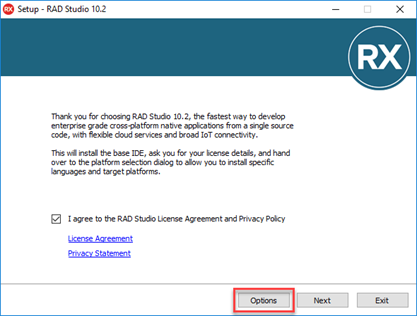
Just a very quick note: I was just installing RAD Studio 10.2.2 when I noticed the installer has an Options button:
So I clicked it to see what options are available and noticed that the "Embarcadero Customer Experience Program" is opted-in by default:
Change NetScaler Password Hash from SHA1 to SHA512
Author: Remko Weijnen13 Dec
This morning I wanted to install the NetScaler patch for the TLS padding vulnerability and of course I made a backup before deploying it.
Note: If you haven’t installed this patch yet I would recommended to do so: see CTX230238 and check out the ROBOT attack -Return Of Bleichenbacher’s Oracle Threat page to check which other products you may have that are vulnerable.
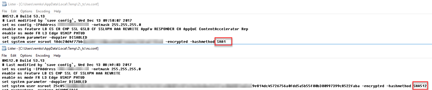
Upon checking the backups (I always download the backup and verify that the archive is intact) I noticed that one of my NetScaler’s uses SHA1 for the password hash whilst the other one uses SHA512:
I thought that this was a little strange as both NetScaler’s are running the exact same build. However one of them (the one that uses SHA512) was reinstalled recently whilst the one using SHA1 has been upgraded.
Profile
Top Posts
- Query Active Directory from Excel
- RNS 510 Startup Logo–My thoughts
- Adding a hidden Exchange mailbox to Outlook
- How rdp passwords are encrypted
- Get Actual CPU Clock Speed with PowerShell
- ClickOnce Applications in Enterprise Environments
- VW RNS 510 Navigation Startup Pictures
- Unattended Installation of IBM System i Access for Windows
- Reading physical memory size from the registry
- Show Client IP Address when using NetScaler as a Reverse Proxy
Recent Comments
Featured Downloads
- AClientFix (13595 downloads )
- AddPrinter2.zip (12854 downloads )
- AdProps (12379 downloads )
- AdSample1 (11432 downloads )
- AMD Radeon Crimson ReLive (29928 downloads )
- Atheros Driver (34019 downloads )
- AutoLogonXP 1.0 (11404 downloads )
- CDZA (9560 downloads )
- ChDrvLetter.zip (11217 downloads )
- ChDrvLetter.zip (14356 downloads )
Blogroll
- Andrew Morgan
- Arnout’s blog
- Assa’s Blog
- Barry Schiffer
- Delphi Praxis
- Ingmar Verheij
- Jedi Api Blog
- Jedi API Library
- Jeroen Tielen
- Kees Baggerman
Categories
- .NET (4)
- Active Directory (28)
- Altiris (36)
- App-V (1)
- Apple (5)
- Application Compatibility (11)
- Automotive (5)
- AWS (1)
- BootCamp (1)
- C# (6)
- C++ (2)
- Citrix (87)
- Delphi (61)
- Embedded (4)
- Exchange (16)
- General (71)
- iPhone (5)
- Java (8)
- Linux (1)
- Lync (2)
- NetScaler (1)
- Oracle (4)
- Other (1)
- Packaging (19)
- PowerShell (56)
- Programming (79)
- Quest (1)
- RES (7)
- script (22)
- ShareFile (1)
- SQL Server (10)
- Strange Error (3)
- Terminal Server (68)
- ThinApp (3)
- ThinKiosk (1)
- Ubuntu (1)
- Unattended Installation (19)
- Uncategorized (51)
- UWP (2)
- Vista (37)
- Visual Studio (1)
- VMWare (26)
- Windows 10 (2)
- Windows 2003 (30)
- Windows 2008 (37)
- Windows 2008 R2 (16)
- Windows 2012 (2)
- Windows 7 (30)
- Windows 8 (4)
- Windows Internals (12)
- Windows XP (16)
Archives
- February 2023 (1)
- October 2022 (3)
- July 2022 (1)
- June 2022 (2)
- October 2019 (1)
- March 2018 (1)
- January 2018 (4)
- December 2017 (3)
- April 2017 (1)
- March 2017 (5)
- February 2017 (4)
- May 2016 (3)
- March 2016 (1)
- October 2015 (2)
- September 2015 (1)
- January 2015 (1)
- August 2014 (1)
- July 2014 (8)
- May 2014 (1)
- November 2013 (1)
- October 2013 (2)
- September 2013 (3)
- August 2013 (4)
- June 2013 (2)
- May 2013 (3)
- April 2013 (5)
- March 2013 (5)
- February 2013 (1)
- January 2013 (5)
- December 2012 (9)
- November 2012 (3)
- October 2012 (3)
- August 2012 (4)
- July 2012 (2)
- June 2012 (1)
- May 2012 (6)
- March 2012 (13)
- February 2012 (12)
- January 2012 (9)
- December 2011 (9)
- November 2011 (4)
- October 2011 (5)
- September 2011 (10)
- August 2011 (10)
- July 2011 (2)
- June 2011 (8)
- May 2011 (12)
- April 2011 (4)
- March 2011 (14)
- February 2011 (8)
- January 2011 (32)
- December 2010 (23)
- November 2010 (19)
- October 2010 (10)
- September 2010 (6)
- August 2010 (1)
- July 2010 (1)
- June 2010 (6)
- March 2010 (7)
- February 2010 (3)
- December 2009 (3)
- November 2009 (11)
- September 2009 (2)
- July 2009 (1)
- June 2009 (5)
- May 2009 (1)
- April 2009 (2)
- March 2009 (3)
- February 2009 (6)
- January 2009 (3)
- December 2008 (8)
- November 2008 (5)
- October 2008 (3)
- September 2008 (3)
- August 2008 (3)
- June 2008 (6)
- May 2008 (2)
- April 2008 (3)
- March 2008 (5)
- January 2008 (3)
- December 2007 (3)
- November 2007 (13)
- October 2007 (10)