Remko Weijnen's Blog (Remko's Blog)
About Virtualization, VDI, SBC, Application Compatibility and anything else I feel like
Archive for the ‘Programming’ Category
JEDI Apilib and JEDI Windows Security Code Library
Author: Remko Weijnen8 Nov
It has been a little silent on the JEDI Apilib project lately, but this will change!
We had some change in the team members: Marcel van Brakel, founder and large contributor of the project has signed off because he no longer actively uses Delphi. Christian Wimmer has joined the team and he is a very promising member.
Christian has been working on a new include model (optional) of the Jedi Apilib which has the advantage that you only need to use one unit (JwaWindows) for the whole library.
Chris has also published the JEDI Windows Security Code Library (Jwscl). This is library that tremendously simplifies using Win32 API calls from Delphi. At this point the library contains:
- Windows Version
- Token
- Impersonation
- Login
- SID
- Access Control List
- Security Descriptor
- Owner, Group, DACL, SACL
- WindowStation
- Desktop
- LSA
- Rights mapping
- Secured Objects Files, Registry (+Inheritance), etc.
- Credentials (Login Dialog)
- Encryption (MS Crypto API)
- Well Known SIDs
- Privileges
- Security Dialogs (The “ACL Editor” you see on the security yab when you rightclick object in Explorer)
- Terminal Sessions
- Unicode + Ansicode
- Vista Elevation
- Vista Integrity Level
Although Jwscl is in beta stage it is already very well useable.
Encrypt RDP password in Python
Author: Remko Weijnen5 Nov
Dirk Schmitz send me his Python version of encrypting the RDP Password:
1 2 3 4 5 | import win32crypt import binascii pwdHash = win32crypt.CryptProtectData(u"MYPASSWORD",u'psw',None,None,None,0) print binascii.hexlify(pwdHash) |
Read the original article here: https://www.remkoweijnen.nl/blog/2007/10/18/how-rdp-passwords-are-encrypted/
How to get Client IP Address?
Author: Remko Weijnen31 Oct
When a client is connected to a Terminal Server Session you can use the Terminal Server API to retrieve the client’s local IP address.
Start by enumerating all sessions with WtsEnumerateSessions and then for each session get the ClientAddress with a call to WTSQuerySessionInformation with the WTSClientAddress parameter. Sound simple, no?
WTSQuerySessionInformation returns a pointer to a WTS_CLIENT_ADDRESS structure. You need to know that the IP address is located at on offset of 2 bytes in the Address member of WTS_CLIENT_ADDRESS.
So here’s a sample:
New Terminal Server API’s in Vista SP1
Author: Remko Weijnen30 Oct
The upcoming Vista SP1 promises 3 new Terminal Server API functions:
- WTSConnectSession : Connects a Terminal Services session to an existing session on the local computer.
- WTSStartRemoteControlSession: Starts the remote control of another Terminal Services session.
- WTSStopRemoteControlSession : Stops a remote control session.
If you look in the Windows 2008 beta you can see that the functions are already implemented (in WtsApi32.dll):
RDP Clipboard Fix
Author: Remko Weijnen25 Oct
Did you ever loose Clipboard functionality (copy/paste) while working with several Terminal Server sessions? I think everyone that works a lot with Terminal Server has experienced this from time to time.
It’s caused by badly behaving applications. Dimitry Vostokov wrote a tool to fix this issue for Citrix (RepairCBDChain.exe), he explains the issue very well on his blog:
Windows has a mechanism to notify applications about clipboard changes. An application interested in such notifications has to register itself in the so called clipboard chain. Windows inserts it on top of that chain and that application is responsible to propagate changes down the chain:
If 3rd-party application forgets to forward notifications down then we have a broken clipboard chain and clipboard changes are not sent via ICA protocol:
Read more at Dimitry’s Blog: http://citrite.org/blogs/dmitryv/2006/12/09/clipboard-issues-explained/
So how can we fix this for Terminal Server then?
(more…)
TSAdminEx
Author: Remko Weijnen23 Oct
You will probably know Microsofts Tool to Manage Terminal Server, it’s called Terminal Services Manager (you will probably know it as TSAdmin). It can be used to view information about terminal servers including all sessions, users, and processes for each terminal server.
I’m currently working on a TSAdmin replacement (codename TSAdminEx). Purpose is to show how to use the Terminal Server API’s and as a little bonus we will add some extra functionality to TSAdminEx.
How to launch a process in a Terminal Session
Author: Remko Weijnen20 Oct
This is an often asked question but the solution is simple:
So how does it work?
First we obtain the user’s primary access token with the WtsQueryUserToken API call. To call this function successfully, the calling application must be running within the context of the LocalSystem account and have the SE_TCB_NAME privilege (LocalSystem has this privilege by default). Since the function returns a primary acces token we can just pass this to CreateProcessAsUser and voila!
A referral was returned from the server
Author: Remko Weijnen19 Oct
Ever tried to run a VBS scripts that queries Active Directory in another domain or from a workstation that is not a domain member? Than you have probably seen this error before:
![]()
![]()
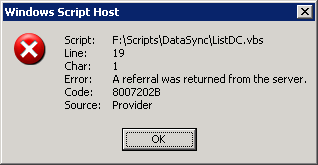
This is because the default settings for Chasing referrals is set to ADS_CHASE_REFERRALS_NEVER.
How rdp passwords are encrypted
Author: Remko Weijnen18 Oct
 Ever wondered how mstsc saves passwords? If you open an RDP file with a text editor like Notepad you can see the encrypted password. In this article I will show you how to encrypt and decrypt these passwords. Besides password recovery this enables you to create rpd files programmatically or perhaps update the password in many rdp files with a batch file.
Ever wondered how mstsc saves passwords? If you open an RDP file with a text editor like Notepad you can see the encrypted password. In this article I will show you how to encrypt and decrypt these passwords. Besides password recovery this enables you to create rpd files programmatically or perhaps update the password in many rdp files with a batch file.
Profile
Top Posts
- Query Active Directory from Excel
- RNS 510 Startup Logo–My thoughts
- Adding a hidden Exchange mailbox to Outlook
- How rdp passwords are encrypted
- Get Actual CPU Clock Speed with PowerShell
- ClickOnce Applications in Enterprise Environments
- VW RNS 510 Navigation Startup Pictures
- Unattended Installation of IBM System i Access for Windows
- Reading physical memory size from the registry
- Show Client IP Address when using NetScaler as a Reverse Proxy
Recent Comments
Featured Downloads
- AClientFix (13595 downloads )
- AddPrinter2.zip (12854 downloads )
- AdProps (12379 downloads )
- AdSample1 (11432 downloads )
- AMD Radeon Crimson ReLive (28037 downloads )
- Atheros Driver (34019 downloads )
- AutoLogonXP 1.0 (11404 downloads )
- CDZA (9560 downloads )
- ChDrvLetter.zip (11217 downloads )
- ChDrvLetter.zip (14356 downloads )
Blogroll
- Andrew Morgan
- Arnout’s blog
- Assa’s Blog
- Barry Schiffer
- Delphi Praxis
- Ingmar Verheij
- Jedi Api Blog
- Jedi API Library
- Jeroen Tielen
- Kees Baggerman
Categories
- .NET (4)
- Active Directory (28)
- Altiris (36)
- App-V (1)
- Apple (5)
- Application Compatibility (11)
- Automotive (5)
- AWS (1)
- BootCamp (1)
- C# (6)
- C++ (2)
- Citrix (87)
- Delphi (61)
- Embedded (4)
- Exchange (16)
- General (71)
- iPhone (5)
- Java (8)
- Linux (1)
- Lync (2)
- NetScaler (1)
- Oracle (4)
- Other (1)
- Packaging (19)
- PowerShell (56)
- Programming (79)
- Quest (1)
- RES (7)
- script (22)
- ShareFile (1)
- SQL Server (10)
- Strange Error (3)
- Terminal Server (68)
- ThinApp (3)
- ThinKiosk (1)
- Ubuntu (1)
- Unattended Installation (19)
- Uncategorized (51)
- UWP (2)
- Vista (37)
- Visual Studio (1)
- VMWare (26)
- Windows 10 (2)
- Windows 2003 (30)
- Windows 2008 (37)
- Windows 2008 R2 (16)
- Windows 2012 (2)
- Windows 7 (30)
- Windows 8 (4)
- Windows Internals (12)
- Windows XP (16)
Archives
- February 2023 (1)
- October 2022 (3)
- July 2022 (1)
- June 2022 (2)
- October 2019 (1)
- March 2018 (1)
- January 2018 (4)
- December 2017 (3)
- April 2017 (1)
- March 2017 (5)
- February 2017 (4)
- May 2016 (3)
- March 2016 (1)
- October 2015 (2)
- September 2015 (1)
- January 2015 (1)
- August 2014 (1)
- July 2014 (8)
- May 2014 (1)
- November 2013 (1)
- October 2013 (2)
- September 2013 (3)
- August 2013 (4)
- June 2013 (2)
- May 2013 (3)
- April 2013 (5)
- March 2013 (5)
- February 2013 (1)
- January 2013 (5)
- December 2012 (9)
- November 2012 (3)
- October 2012 (3)
- August 2012 (4)
- July 2012 (2)
- June 2012 (1)
- May 2012 (6)
- March 2012 (13)
- February 2012 (12)
- January 2012 (9)
- December 2011 (9)
- November 2011 (4)
- October 2011 (5)
- September 2011 (10)
- August 2011 (10)
- July 2011 (2)
- June 2011 (8)
- May 2011 (12)
- April 2011 (4)
- March 2011 (14)
- February 2011 (8)
- January 2011 (32)
- December 2010 (23)
- November 2010 (19)
- October 2010 (10)
- September 2010 (6)
- August 2010 (1)
- July 2010 (1)
- June 2010 (6)
- March 2010 (7)
- February 2010 (3)
- December 2009 (3)
- November 2009 (11)
- September 2009 (2)
- July 2009 (1)
- June 2009 (5)
- May 2009 (1)
- April 2009 (2)
- March 2009 (3)
- February 2009 (6)
- January 2009 (3)
- December 2008 (8)
- November 2008 (5)
- October 2008 (3)
- September 2008 (3)
- August 2008 (3)
- June 2008 (6)
- May 2008 (2)
- April 2008 (3)
- March 2008 (5)
- January 2008 (3)
- December 2007 (3)
- November 2007 (13)
- October 2007 (10)