Remko Weijnen's Blog (Remko's Blog)
About Virtualization, VDI, SBC, Application Compatibility and anything else I feel like
Archive for the ‘Uncategorized’ Category
Google Earth fix for XenApp, RDSH & Horizon
Author: Remko Weijnen20 Feb
 Both Google Earth and Google Earth Enterprise do not work correctly for multiple users on shared Hosted Shared Desktops (I still prefer to call it Server Based Computing but that’s likely because I’m an oldtimer).
Both Google Earth and Google Earth Enterprise do not work correctly for multiple users on shared Hosted Shared Desktops (I still prefer to call it Server Based Computing but that’s likely because I’m an oldtimer).
Problem summary
So let’s look at the actual issue: the first user on a server is able to launch Google Earth but for any subsequent users on the same server Google Earth fails silently.
Problem details
Google Earth uses various synchronization objects such as Events and Mutexes but registers those in the \Global namespace instead of the \Local namespace.
Show Client IP Address when using NetScaler as a Reverse Proxy
Author: Remko Weijnen10 Feb
 Recently I switched over my blog from a hoster to a self hosted VM. In my setup I am using Citrix NetScaler as a reverse proxy.
Recently I switched over my blog from a hoster to a self hosted VM. In my setup I am using Citrix NetScaler as a reverse proxy.
Simular to when you’re using a 3rd party reverse proxy such as CloudFlare you will see the IP address from the reverse proxy instead of the actual Client IP Address on your webserver.
This means that your logging will all show the same, internal, IP address and that IP Based Access Rules will not work.
Fortunately this is easy to solve by having NetScaler add the Client IP Address in the headers and rewriting the address on your webserver.
Blog improvements
Author: Remko Weijnen7 Feb
When I started this blog in 2007 (wow that’s almost 10 years ago) I went for a cheap web hoster with a reasonable performance to host it.
In the beginning performance was acceptable but over the years it has degraded and of course user experience standards have changed.
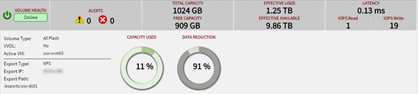
I decided it was time to do something about it so I’ve moved the blog from a shared platform to my own server.
This server is running on optimized flash storage where most writes are DeDuplicated and never actually hits the flash disks:
Twitter Analytics and AdBlock Plus
Author: Remko Weijnen28 Aug
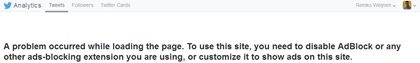
Twitter has opened access to Analytics for all users. However when you use an Ad Blocker, like Adblock Plus, you’ll get the following error:
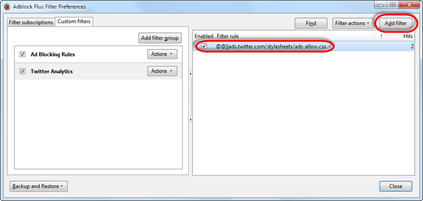
For Adblock Plus you can fix this by adding a filter: go to Filter Preferences and on the "Custom filters" tab add a new filter within a filter group (or create a filter group for this rule).
Use this as a filter rule:
@@||ads.twitter.com/stylesheets/ads-allow.css
And don’t forget to Enable the rule!
EDIT: Twitter user @Ertraeglichkeit mentioned a different method:
Set alert parameters with Visual Studio Authoring Extensions
Author: Remko Weijnen18 Jul
 In a SCOM Management Pack Custom Properties can be used for Alert Description and Notification as described in this blog by Kevin Holman.
In a SCOM Management Pack Custom Properties can be used for Alert Description and Notification as described in this blog by Kevin Holman.
In my case I wanted to add the Display Name and the Performance Counter Value in a Performance Threshold Monitor. In XML it would look this this:
1 2 3 4 5 6 7 8 9 10 | <alertsettings alertmessage="Memory.Usage.AlertMessage"> <alertonstate>Error</alertonstate> <autoresolve>true</autoresolve> <alertpriority>Normal</alertpriority> <alertseverity>MatchMonitorHealth</alertseverity> <alertparameters> <alertparameter1>$Target/Host/Property[Type="System!System.Entity"]/DisplayName$</alertparameter1> <alertparameter2>$Data/Context/Value$</alertparameter2> </alertparameters> </alertsettings> |
But how to add these parameters when using the System Center 2012 Visual Studio Authoring Extensions?
Cannot connect to iTunes Store after enabling https scanning in Sophos UTM
Author: Remko Weijnen16 Jul
![]() I am currently implementing Sophos UTM and I quite like this solution. It is free up for home usage and can easily be installed on a hypervisor.
I am currently implementing Sophos UTM and I quite like this solution. It is free up for home usage and can easily be installed on a hypervisor.
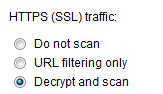
I wanted to scan encrypted traffic (ssl) as well so I activated the "Decrypt and scan" option:
When testing this on one of my iPad’s I noticed that the App Store didn’t work properly anymore.
When I tried to update applications I got the following error: "Cannot connect to iTunes Store". Additionally when I searched for Apps the search would return no results.
non-existent schema type ‘Snmp!System.SnmpVarBindsSchema’ error in SCOM
Author: Remko Weijnen13 Jul
 Today I encounterd what seems to be a bug in the System Center 2012 Visual Studio Authoring Extensions. I wanted to define a Performance Collection Rule that reads out the percentage of free memory from an SNMP device.
Today I encounterd what seems to be a bug in the System Center 2012 Visual Studio Authoring Extensions. I wanted to define a Performance Collection Rule that reads out the percentage of free memory from an SNMP device.
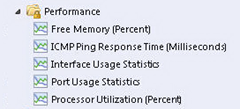
Since the device returns only the percentage of used memory I needed to use the ComputedPerfProvider provider to substract the used memory percentage from 100.
I could of course report used memory instead of free memory but I wanted the resulst to appear in the default SCOM Performance View, which only lists Free Memory:
Where to find System.NetworkManagement.Monitoring.mp?
Author: Remko Weijnen13 Jul
 I am currently working on a Management Pack for SCOM and I have studies a few examples on adding processor and memory counters.
I am currently working on a Management Pack for SCOM and I have studies a few examples on adding processor and memory counters.
These examples all reference a Management Pack named "System.NetworkManagement.Monitoring.mp" but this Management Pack is not bundled with the System Center 2012 Visual Studio Authoring Extensions.
Aaron Parker was talking about the uninstall guid in his session “Hands off my Golden Image Redux” at Citrix Synergy.
I remembered that I had written a small PowerShell script to read out the uninstall GUID from an MSI file. This way you do not need to actually install the software to determine the uninstall GUID.
How does that work?
There is a logical relation between the MSI Product Code property and the install guid. In this example I’ve taken install_flash_player_11.8.800.174_active_x.msi as an example.
The Uninstall key is HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\A2E504D3D31C0D5409F28F3FDD565AD9
The interesting part of it is the GUID:
A2E504D3D31C0D5409F28F3FDD565AD9
If we look into the MSI properties with (Super)Orca we see:
If we compare those GUIDS:
Uninstal {A2E504D3-D31C-0D54-09F2-8F3FDD565AD9}
Product Code{3D405E2A-C13D-45D0-902F-F8F3DD65A59D}
We can see that we need to apply the following logic:
· First 8 bytes must be swapped right to left
· Next 4 bytes (skipping the hyphen) also swapped right to left
· Next 4 bytes (skipping the hyphen) also swapped right to left
· Next 4 bytes (skipping the hyphen) also swapped right to left
· Last 12 bytes must be byte swapped per byte (F8 -> 8F, F3 -> 3F etc).
Knowing that we can make life easier with PowerShell:
[posh]function Get-Property ($Object, $PropertyName, [object[]]$ArgumentList)
{
return $Object.GetType().InvokeMember($PropertyName, ‘Public, Instance, GetProperty’, $null, $Object, $ArgumentList)
}
function Invoke-Method ($Object, $MethodName, $ArgumentList)
{
return $Object.GetType().InvokeMember($MethodName, ‘Public, Instance, InvokeMethod’, $null, $Object, $ArgumentList)
}
function GetMsiProductCode([string]$path)
{
$msiOpenDatabaseModeReadOnly = 0
$Installer = New-Object -ComObject WindowsInstaller.Installer
$Database = Invoke-Method $Installer OpenDatabase @($path, $msiOpenDatabaseModeReadOnly)
$View = Invoke-Method $Database OpenView @(“SELECT Value FROM Property WHERE Property=’ProductCode'”)
Invoke-Method $View Execute | Out-Null
$Record = Invoke-Method $View Fetch
if ($Record)
{
Write-Output (Get-Property $Record StringData 1)
}
}
cls
$path = “c:\Users\rweijnen\Desktop\install_flash_player_11.8.800.174_active_x.msi”
$item = “” | Select-Object Path, ProductCode, UninstallGuid, UninstallRegistry
$item.Path = $path
$item.ProductCode = (GetMsiProductCode $item.Path)
$DestGuid = ([regex]::Matches($item.ProductCode.Substring(1,8),’.’,’RightToLeft’) | ForEach {$_.value}) -join ”
$DestGuid += ([regex]::Matches($item.ProductCode.Substring(10,4),’.’,’RightToLeft’) | ForEach {$_.value}) -join ”
$DestGuid += ([regex]::Matches($item.ProductCode.Substring(15,4),’.’,’RightToLeft’) | ForEach {$_.value}) -join ”
$DestGuid += ([regex]::Matches($item.ProductCode.Substring(20,2),’.’,’RightToLeft’) | ForEach {$_.value}) -join ”
$DestGuid += ([regex]::Matches($item.ProductCode.Substring(22,2),’.’,’RightToLeft’) | ForEach {$_.value}) -join ”
for ($i=25 ; $i -lt 37 ; $i = $i + 2)
{
$DestGuid += ([regex]::Matches($item.ProductCode.Substring($i,2),’.’,’RightToLeft’) | ForEach {$_.value}) -join ”
}
$item.UninstallGuid = “{” + ([Guid]$DestGuid).ToString().ToUpper() + “}”
$item.UninstallRegistry = “HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\{0}” -f $DestGuid
$item | Format-List
Sample output:
Path : c:\Users\rweijnen\Desktop\install_flash_player_11.8.800.174_active_x.msi
ProductCode : {3D405E2A-C13D-45D0-902F-F8F3DD65A59D}
UninstallGuid : {A2E504D3-D31C-0D54-09F2-8F3FDD565AD9}
UninstallRegistry : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\A2E504D3D31C0D5409F28F3FDD565AD9
[/posh]
My presentation at E2EVC in Rome
Author: Remko Weijnen29 Oct
 I will be presenting a session at E2EVC in Rome next weekend.
I will be presenting a session at E2EVC in Rome next weekend.
Recently I published an article on my blog that shows how to run an executable of choice when the Citrix Receiver exits.
 In this session I will show you how to find such undocumented features in applications step by step. Using this example we will open the Citrix Receiver in Ida Pro and disassemble it.
In this session I will show you how to find such undocumented features in applications step by step. Using this example we will open the Citrix Receiver in Ida Pro and disassemble it.
Using public resources such as the Citrix Public Symbol Server we can analyze, understand and finally make the code more readable.
I will try to make this session not an “enter the matrix one” but one that could be considered as an intro into using Ida Pro for reverse engineering and app compat fixing.
Hope to see you all in Rome, my session is scheduled Friday November 1 from 18.30 – 19.15. There will be room for questions so feel free to take your own Crapplication™ and ask about it after the session.
See you in Rome!
Profile
Top Posts
- Query Active Directory from Excel
- RNS 510 Startup Logo–My thoughts
- Adding a hidden Exchange mailbox to Outlook
- How rdp passwords are encrypted
- Get Actual CPU Clock Speed with PowerShell
- ClickOnce Applications in Enterprise Environments
- VW RNS 510 Navigation Startup Pictures
- Unattended Installation of IBM System i Access for Windows
- Reading physical memory size from the registry
- Show Client IP Address when using NetScaler as a Reverse Proxy
Recent Comments
Featured Downloads
- AClientFix (13595 downloads )
- AddPrinter2.zip (12854 downloads )
- AdProps (12379 downloads )
- AdSample1 (11432 downloads )
- AMD Radeon Crimson ReLive (29588 downloads )
- Atheros Driver (34019 downloads )
- AutoLogonXP 1.0 (11404 downloads )
- CDZA (9560 downloads )
- ChDrvLetter.zip (11217 downloads )
- ChDrvLetter.zip (14356 downloads )
Blogroll
- Andrew Morgan
- Arnout’s blog
- Assa’s Blog
- Barry Schiffer
- Delphi Praxis
- Ingmar Verheij
- Jedi Api Blog
- Jedi API Library
- Jeroen Tielen
- Kees Baggerman
Categories
- .NET (4)
- Active Directory (28)
- Altiris (36)
- App-V (1)
- Apple (5)
- Application Compatibility (11)
- Automotive (5)
- AWS (1)
- BootCamp (1)
- C# (6)
- C++ (2)
- Citrix (87)
- Delphi (61)
- Embedded (4)
- Exchange (16)
- General (71)
- iPhone (5)
- Java (8)
- Linux (1)
- Lync (2)
- NetScaler (1)
- Oracle (4)
- Other (1)
- Packaging (19)
- PowerShell (56)
- Programming (79)
- Quest (1)
- RES (7)
- script (22)
- ShareFile (1)
- SQL Server (10)
- Strange Error (3)
- Terminal Server (68)
- ThinApp (3)
- ThinKiosk (1)
- Ubuntu (1)
- Unattended Installation (19)
- Uncategorized (51)
- UWP (2)
- Vista (37)
- Visual Studio (1)
- VMWare (26)
- Windows 10 (2)
- Windows 2003 (30)
- Windows 2008 (37)
- Windows 2008 R2 (16)
- Windows 2012 (2)
- Windows 7 (30)
- Windows 8 (4)
- Windows Internals (12)
- Windows XP (16)
Archives
- February 2023 (1)
- October 2022 (3)
- July 2022 (1)
- June 2022 (2)
- October 2019 (1)
- March 2018 (1)
- January 2018 (4)
- December 2017 (3)
- April 2017 (1)
- March 2017 (5)
- February 2017 (4)
- May 2016 (3)
- March 2016 (1)
- October 2015 (2)
- September 2015 (1)
- January 2015 (1)
- August 2014 (1)
- July 2014 (8)
- May 2014 (1)
- November 2013 (1)
- October 2013 (2)
- September 2013 (3)
- August 2013 (4)
- June 2013 (2)
- May 2013 (3)
- April 2013 (5)
- March 2013 (5)
- February 2013 (1)
- January 2013 (5)
- December 2012 (9)
- November 2012 (3)
- October 2012 (3)
- August 2012 (4)
- July 2012 (2)
- June 2012 (1)
- May 2012 (6)
- March 2012 (13)
- February 2012 (12)
- January 2012 (9)
- December 2011 (9)
- November 2011 (4)
- October 2011 (5)
- September 2011 (10)
- August 2011 (10)
- July 2011 (2)
- June 2011 (8)
- May 2011 (12)
- April 2011 (4)
- March 2011 (14)
- February 2011 (8)
- January 2011 (32)
- December 2010 (23)
- November 2010 (19)
- October 2010 (10)
- September 2010 (6)
- August 2010 (1)
- July 2010 (1)
- June 2010 (6)
- March 2010 (7)
- February 2010 (3)
- December 2009 (3)
- November 2009 (11)
- September 2009 (2)
- July 2009 (1)
- June 2009 (5)
- May 2009 (1)
- April 2009 (2)
- March 2009 (3)
- February 2009 (6)
- January 2009 (3)
- December 2008 (8)
- November 2008 (5)
- October 2008 (3)
- September 2008 (3)
- August 2008 (3)
- June 2008 (6)
- May 2008 (2)
- April 2008 (3)
- March 2008 (5)
- January 2008 (3)
- December 2007 (3)
- November 2007 (13)
- October 2007 (10)